INTRODUCTION
- Cyber threats are constantly evolving, and the dynamic nature of the cyber domain dictates the need for prioritization of cyber security in the nuclear security architecture.
- Nearly 1.16 million cases of cyber-attacks were reported in 2020, up by nearly three times from 2019, according to government data presented in the Parliament.
- Cyber security is a pillar of nuclear security. Various incidents, such as in 2015 Hanford nuclear site in the USA, Gundremmingen nuclear power plant in 2016 in Germany have demonstrated the vulnerability of nuclear facilities and systems to cyber threats.
What is Nuclear Security?
As defined by the International Atomic Energy Agency (IAEA), nuclear security is the prevention of, detection of, and response to, criminal or intentional unauthorized acts involving or directed at nuclear material, other radioactive material, associated facilities, or associated activities.
|
- Historically in India, there has been little deliberation to address cyber risks pertaining to civilian and military nuclear facilities.
- In India’s cyber security policy has remained inadequate according to the changing dynamics and emerging threats of cyber warfare and attacks.
- Recently in late 2019, the Indian Space Research Organisation (ISRO) headquarters in Bengaluru and the Kudankulam nuclear power plant in Tamil Nadu both suffered breaches in their security which is related to the malware attack known as D track
- As nuclear infrastructure becomes increasingly more integrated with cyber technologies, there is a risk of its hacking, disruption, and potential for sabotage also increases, it’s high time to revisit the policies in place for nuclear facilities.
NUCLEAR ENERGY
- Nuclear energy is a form of energy released from the nucleus, the core of atoms, made up of protons and neutrons.
- Nuclear sources of energy can be produced in two ways:
- fission – when nuclei of atoms split into several parts
- fusion – when nuclei fuse
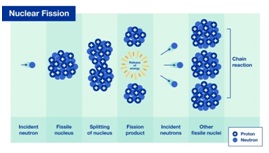 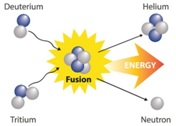
- Nuclear fuel is the fuel that is used in a nuclear reactor to sustain a nuclear chain reaction.
- These fuels are fissile, and the most common nuclear fuels are the radioactive metals uranium-235 and plutonium-239.
- All processes involved in obtaining, refining, and using this fuel make up a cycle known as the nuclear fuel cycle.
|
CONSEQUENCES AND HAZARDS OF CYBER ATTACK IN NUCLEAR DOMAIN
Cyber breaches increase the likelihood of vulnerabilities in nuclear systems
- The infiltration of malware and viruses into the systems can occur at several stages in the production and supply chain, through embedded codes which can lead to compromise the weapons during conflict or their ability to act as deterrents.
Cyber-attack can undermine communications systems
- It can prevent the flow of crucial information, obtaining confidential information, disruption in dual-use communications, etc, and prevent the use of communication channels to de-escalate a crisis.
Cyber attacks can be vulnerable to human fallibility
- Nuclear systems and their security are predicated upon human judgment and there is the possibility of false information from warning systems as a result of human error, which could be an accident or a deliberate act.
Cyber-attacks have economic, operational, and reputational costs
- A cyber-attack on a specific component exposes vulnerabilities in the entire system; this should call for more spending on security practices and infrastructure at every level, therefore increasing the operational cost.
Impact on relations with other countries
- Any breach of safety gives rise to distrust of the systems and may negatively impact relations with allies and adversaries alike, and questioning of the reliability of a country.
Risk of insider threat
- After all, nuclear systems are managed and operated by individuals with different security clearances, which also exposes the structure to cyber infiltrations from within, such as creating and exploiting software vulnerabilities, introducing viruses, and sharing critical information with adversaries.
Breach of sensitive information
- Cyber-attacks may result in theft of nuclear/radioactive materials, radiation release due to malicious intent of adversaries, theft of sensitive information about nuclear facilities, reactor designs, etc.
- Access to nuclear facilities through cyber-attacks can result in direct physical access to the facility, materials, and information which add to challenges of the interconnectedness of cyber and physical nuclear security.
Nuclear use for Terrorism
- The various cyber-attacks can lead to the stealing of sensitive information which could be used by various terrorist organizations to develop nuclear capabilities
|
In Iran, particularly the 2010 Stuxnet attack on the country’s Natanz uranium enrichment plant, highlight the dangers of cyber attacks and cyber warfare for a country with nuclear systems.
More recently, the attack on the Natanz facility in 2021, which targeted the industrial control systems and destroyed the power supply to centrifuges used to create enriched uranium, underscored the sophistication and capabilities of the cyber domain.
|
Cyber Security in Indian Context
Given the sensitive nature of nuclear materials and infrastructures, it is important to create policies that offer both short-term and long-term solutions and accommodate change with changing security needs and contexts. Following are the steps taken by Government for cyber security
- National cyber security policy: In 2013, the Department of Electronics and Information Technology released a policy framework—the first of its kind—to articulate a national cyber security policy.
- The policy document sets out guidelines and objectives for the protection of the country against cyber-attacks.
- However, this policy is lacking in any explicit mention of the correlation between cyber and nuclear security.
- Defence Cyber Agency: In 2013 the government also announced the setting up of a ‘Defence Cyber Agency’ that will create mechanisms within the security infrastructure to battle cyber warfare and cyber infiltration in India’s defense networks.
- NTRO: India also has a National Technical Research Organisation (NTRO) tasked with “cyber intelligence and cyber counterintelligence”.
- The body is independent of the technical wings of other government agencies.
- CERT-In: A national-level Computer Emergency Response Team (CERT-In), created in 2004, works to coordinate all efforts undertaken for cyber security emergency response and crisis management.
- Other Important Organizations include:
- Crime and Criminal Tracking Network System (CCTNS)
- National Cyber Coordination Centre (NCCC)
- National Critical Information Infrastructure Protection Centre (NCIIPC)
|
CASE STUDY
- In September 2019, the cyber-attack on India’s Kudankulam Nuclear Power Plant happened which has highlighted the importance of strengthening the country’s cyber-nuclear security infrastructure.
- The malware attack was on the administrative system, though it has not affected any plant control devices or instrumentation.
- Cyber security researchers suggested that the attack was caused by a DTRACK virus developed by a group linked to North Korea.
- ISRO also confirmed that it was alerted to a breach attempt by the same virus that targeted Kudankulam.
- Though the attack was limited to the administrative systems, it has exposed serious vulnerabilities in the security of the country’s nuclear facilities.
- It has been noted in previous instances of cyber-attacks that air-gaps provide limited protection on their own and are often under-maintained.
- A large amount of data had been taken from the administrative network, implying the possibility of future attacks on more critical systems at the plant.
- Thus, it is important to strengthen systems against cyber threats using preventive access tools such as “firewalls, anti-virus programs, air gaps, and unidirectional gateways.
|
- A new Cyber Security Policy must fill the inadequacies in the current one so that India can address the evolving challenges to cyber security in the nuclear domain.
Cyber-Nuclear Security in the Global Context and Key Recommendations
Cyber security is not just a national challenge, it should be looked upon in a global context, therefore, it requires global solutions.
- Effective collaboration: In the nuclear context, it is imperative that similar like-minded nations collaborate, exchange useful information, and share best practices to combat the rising threat of cyber-attacks in the nuclear domain.
- Collaboration with such international actors would provide India with the opportunity to learn and incorporate the learnings and best practices into the context of the country’s cyber-nuclear infrastructure.
- Required area of cooperation: Various other partners such as the United Kingdom and Russia, India can collaborate to better equip its cyber-nuclear infrastructure. These agreements cover several areas of cooperation such as the exchange of information, expertise on reactor designs, nuclear safety, etc.
- This can be conducted through technology exchange, exchange of experts, information-sharing agreements, as well as joint exercises and workshops, to better equip the security infrastructure at nuclear systems to counter cyber challenges.
- Involvement of private sectors: India’s largely indigenously developed nuclear weapons program and nuclear fuel cycle capabilities for civilian use are wholly controlled by the government, here the involvement of the private sector can be beneficial.
- Involvement of expertise in policy formulation: The industry's expertise from the nuclear field has been a part of cyber security policies for countries like the United Kingdom, and India should similarly incorporate their involvement into the country’s cyber security policy.
Cyber security policies of Japan, the United Kingdom, and the United States
|
Japan
|
US
|
UK
|
|
Key governing body/act
|
Basic Act on Cyber security (2014)
|
United States Cyber Command
|
National Cyber Security Centre
|
|
Mission
|
Free, fair, and secure cyberspace, protection from cyber-attacks and disruption of social systems.
|
Cyberspace planning and operations to defend and advance national interests in collaboration with domestic and international partners
|
Practical guidance of cyber security, response to cyber incidents, collaboration with industry experts, reduction of risks by securing public and private networks
|
|
Identification
|
Actors involved in critical information for national security need to keep in mind that critical information could become a possible target of global cyber attackers
|
Virtual private networks and hidden supply chain connections, privilege escalation, roaming notebooks, wireless access points, embedded exploits in software and hardware, or maintenance entry points
|
Cyber security is identified as a Tier 1 threat in the National Security Strategy (alongside terrorism, war, and natural disasters)
|
|
Measures & counter-measures
|
Relevant actors will work to increase awareness of cybersecurity for all people involved in advanced technology, and take necessary measures, including enhancing monitoring of and response capabilities against cyber-attacks from abroad; tightening the examination and verification of goods and services obtained externally; strengthening collaboration between the public and private sectors for information sharing and others
Nuclear: Calls for strong public-private partnerships to protect critical information infrastructure (CII)
Consider information-sharing arrangements for the protection of nuclear materials
|
Improve supply chain management, risk management, information technology activities, strengthen, security of sensitive government information, improve transportation cyber security
Nuclear: Modernising its integrated communications system to have efficient and integrated nuclear systems
|
Close coordination with the National Crime Agency.
Develop cyber skills, provide threat intelligence and expert advice with government and industry professionals
Work closely with individuals and agencies involved in owning and operating critical national infrastructure to ensure essential services.
Nuclear: Protect civilian nuclear sector against cyber-attacks.
Build resilience to detect, mitigate and contain cyber-attacks.
|
Important International Organization for Cyber Security
- Budapest Convention on Cyber Security
- International Governance Forum (IGF)
- International Telecommunication Union (ITU)
CONCLUSION
In the present context with the rapid nature of technological advancements, modernizing of nuclear systems and facilities cyber security plays a vital role that has to be deliberated. The forefront of technological advancements and various measures to prepare for consequences and various scenarios should be lead by government policies, even as the participation of the private sector is encouraged.
Indeed, threats are constantly evolving and the risks to critical infrastructure cannot be ignored. The onus to mitigate these risks lies with a country’s ability to develop robust cyber security measures that account for existing threats and allow for necessary changes for those others that may not exist with more spending on infrastructure and R&D.
Finally, the primary point of concern for India’s nuclear systems in terms of cyber risks and threats remains the lack of importance given to a clear, concise, and robust policy framework which has to be relooked soon.